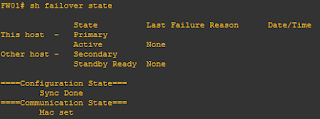
The fail-over configuration requires two identical security appliances connected to each other through a dedicated fail-over link and, optionally, a state full fail-over link. The health of the active interfaces and units is monitored to determine if specific fail-over conditions are met. If those conditions are met, fail-over occurs.
Active/Standby Fail-over lets you use a standby security appliance to take over the functionality of a failed unit. When the active unit fails, it changes to the standby state while the standby unit changes to the active state. The unit that becomes active assumes the IP addresses, or, for a transparent firewall, the management IP address, and MAC addresses of the failed unit and begins to pass traffic.
First you should have two identical ASAs with fail-over feature enabled. you can verify it by issuing following command. If not you have purchase a license.
#show version
Primary Firewall
FW01(config)#failover
2. Set FW as primary or secondary. FW01 configured as primary in given example.
FW01(config)#failover lan unit primary
3. Set the failover link which use to synchronize each other. Ge3 is configured as failover link and "failover-interface" is set as name of the interfaces in both FWs in given example.
FW01(config)#failover lan interface failover-interface GigabitEthernet3
4.Set failover interface primary and secondary ip addresses.
FW01(config)#failover interface ip failover-interface 10.200.190.17 255.255.255.252 standby 10.200.190.18
Secondary Firewall
FW02(config)#failover
2. Set FW as primary or secondary. FW02 configured as primary in given example.
FW02(config)#failover lan unit secondary
3. Set the failover link which use to synchronize each other. Ge3 is configured as failover link and "failover-interface" is set as name of the interfaces in both FWs in given example.
FW02(config)#failover lan interface failover-interface GigabitEthernet3
4.Set failover interface primary and secondary ip addresses.
FW02(config)#failover interface ip failover-interface 10.200.190.17 255.255.255.252 standby 10.200.190.18
Done!!! :)
You can verify the whether it is working properly or not by issuing following command.